Mathew J. Schwartz
Many questions persist about bitcoin and other cryptocurrencies. But as the value of bitcoin, in particular, has continued to soar, cybercriminals have increasingly turned to obtaining all types of cryptocurrency by any ruthless means necessary. Here are nine trends and observations: Cryptocurrency mining refers to solving computationally intensive mathematical tasks, which, in the case of bitcoin, are used to verify the blockchain, or public ledger, of transactions. As an incentive, anyone who mines for cryptocurrency has a chance of getting some cryptocurrency back as a reward.
Legitimate mining enterprises typically involve server farms and face sky-high electricity bills. Predictably, many criminals opt to take a shortcut by infecting victims with cryptocurrency-mining malware.
"The actual process of cryptocurrency mining is perfectly legal, though there are groups of people who hoodwink unwitting users into installing mining software on their computers, or exploiting software vulnerabilities to do so," Evgeny Lopatin and Vladas Bulavas, security researchers at Moscow-based security firm Kaspersky Lab, say in a blog post. "This results in threat actors receiving cryptocurrency, while their victims' computer systems experience a dramatic slowdown."
2. Monero Mining Malware Is Spreading
While bitcoin may be eating up the headlines thanks to its five-figure U.S. dollar value - up from less than $1,000 at the beginning of the year - Avast says the vast majority of cryptocurrency mining malware that it's recently spotted has focused on mining monero, another cryptocurrency that's currently worth about $200. Of course that raises the obvious question: Why not mine for bitcoin?
"While bitcoin is widely used, it doesn't keep transactions private and is more difficult to mine compared to monero, which can be reasonably mined using a browser's CPU power," Avast security researcher Denis Konopiský says in a blog post.
Monero, meanwhile, was designed with privacy in mind, "which also comes in handy for the cybercriminals if they want to obscure their activities," Konopiský says. "Monero uses three different privacy technologies to hide the sender, amount being sent and the recipient, obscuring transaction details."
Cybercriminals seeking free mining power continue to be resourceful. Earlier this year, attackers adapted cryptocurrency mining malware named Adylkuzz to attack a flaw in Windows server block messaging that was revealed by the Shadow Brokers. Some security researchers see links between the Adylkuzz campaign, the WannaCry outbreak and the Lazarus hacking team connected to the cash-strapped North Korean government.
3. AV Software Can Block Cryptocurrency Malware
Cryptocurrency malware is like any other malware in that if it gets detected by anti-virus software, the AV software can block it.
Avast says that on Sunday, users of its anti-virus software collectively saw 35 million attempts to infect them with a JavaScript cryptocurrency miner, which it refers to as "JS:Miner-I," and which its software blocked.
This was a massive spike in detected cryptocurrency mining JavaScript malware infection attempts, Avast says, adding that all involved the Google Chrome browser.
"We suspect the JavaScript code was injected into a Google Chrome extension, as the files blocked as JS:Miner-I were in Chrome's blob_storage, which is a folder used by extensions and add-ons to store data," Konopiský says. "While we cannot say for sure, we believe two things could have happened here: either this is a malicious campaign that was effectively spread, or a popular extension was modified to include the miner."
4. DDoS Attackers Seek Price Fluctuations
From July to September, 74 percent of all bitcoin exchanges were targeted with distributed denial-of-service attacks, report researchers at the security firm Imperva Incapsula in a blog post. Their analysis is based on more than 5,700 network and application layer DDoS attacks that it detected and blocked during that time period.
Cryptocurrency exchanges were the eighth most targeted sector by DDoS attackers, following such sectors as gambling, gaming, internet services, financial services and retailers.
Top DDoS-Attacked Industries 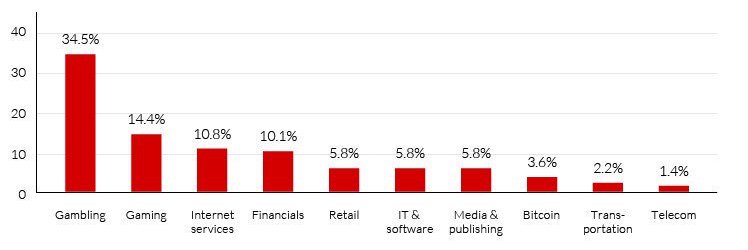 Based on number of targeted organizations from July to September. (Source: Imperva)
Based on number of targeted organizations from July to September. (Source: Imperva)
 Based on number of targeted organizations from July to September. (Source: Imperva)
Based on number of targeted organizations from July to September. (Source: Imperva)
"From extortionists that launch ransom DDoS attacks to more professional offenders working as hired guns for competitors, DDoS attackers are always 'following the money,'" Imperva says. "In this specific case, DDoS attacks could also be an attempt to manipulate bitcoin prices, a tactic attackers have been known to use in the past."
Many DDoS attacks are launched by botnets - networks of malware-infected endpoints. These zombie systems receive attack instructions from a command-and-control server, aka botnet herder, that collectively allow them to launch massive attacks. Such attacks are typically "cybercrime as a service" offerings, often advertised as being stresser/booter services.
From July to September, the greatest volume of DDoS attacks launched by malware-infected PCs were launched in China, the United States, India and Russia. More recently, attacks were launched from Vietnam and Turkey, according to Imperva, which says it's not clear what accounts for the rise in attacks launched by infected devices in those two nations.
Top DDoS Botnet Locations 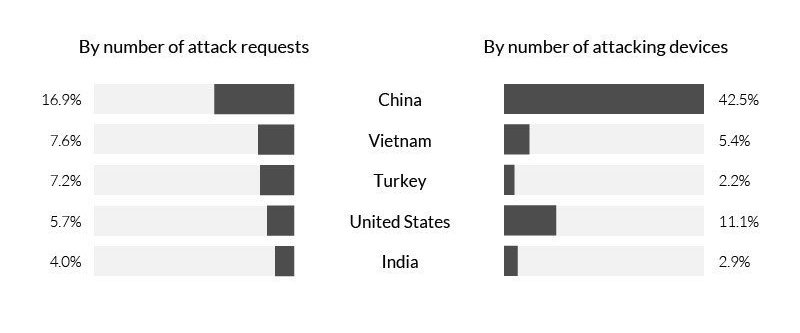 From July to September
From July to September
 From July to September
From July to September
5. A Mining Marketplace Was Recently Hacked
Cryptocurrency exchanges aren't hackers' only target.
On Thursday, Slovenia-based digital currency marketplace NiceHash announced in a statement posted to Reddit that it was suspending operations for at least 24 hours after detecting that hackers had breached its systems and stolen 4,700 bitcoins, which at current values are worth more than $74 million.
NiceHash, the world's largest cryptocurrency mining marketplace, allows registered users to buy or rent cryptocurrency mining power from each others' servers. In the wake of the breach, it has advised all users to change their passwords.
The company's head of marketing, Andrej P Skraba, tells Reuters this was "a highly professional attack with sophisticated social engineering" and says it's working with law enforcement as "a matter of urgency."
6. Malware Can Steal From Wallets
Malware has long targeted cryptocurrency data. In 2016, an update to the Dridex banking Trojan began scanning infected systems for cryptocurrency wallet manager files to steal, security researchers say.
In August, the Trickbot banking Trojan was updated to launch web injection attacks against users of the Coinbase website. Coinbase operates exchanges for bitcoin, ethereum, litecoin and other cryptocurrencies. By using web injection attacks - often waged against online banking customers - attackers could take control of a victim's PC and transfer all of a user's cryptocurrency to attacker-controlled wallets, while disguising the attack (see Zeus Banking Trojan Spawn: Alive and Kicking).
7. Quant Loader Malware Refines Automation
Stealing static wallet files stored on PCs or servers continues to grow easier, thanks to more automated attack tools that have come to market.
For example, Forcepoint, a U.S. security firm owned by defense contractor Raytheon and formerly known as Websense, says it has spotted an update to a Trojan downloader - malware designed to install more malware - that ransacks infected systems for cryptocurrency wallets that store bitcoin, terracoin, peercoin/ppcoin and primecoin.
Previously, this Quant Loader malware, sold on cybercrime markets by "MrRaiX," attempted to distribute the Pony downloader - often used to distribute banking Trojans and steal passwords - as well as Locky ransomware.
The latest versions of Quant, however, download two pieces of software - MBS and Z*Stealer - that are designed to steal cryptocurrency wallet data and which were also developed by MrRaiX, Forcepoint says. Both then function as Quant modules, in the form of DLL files that the main executable can call. Those files are active by default but can be disabled.
 Online advertisement for MBS. (Source: Forcepoint)
Online advertisement for MBS. (Source: Forcepoint)
"These two modules are still sold separately: MBS can be bought separately for $100 for a full license and an additional $15 for every update while Z*Stealer would be $100 for a full license with free updates, or $55 for a base license and an additional $15 for every update," Forcepoint says. "This is as compared to a recent advert offering five full Quant licenses for $275."
Bundling the modules makes it easier for "unskilled" Quant users to automatically steal wallet data, Forcepoint says. "While the software maintains the ability to drop custom payloads, the vast majority of the attacks we saw did not bother to use this capability."
8. Problems Predate Mt Gox's Meltdown
Attacks against cryptocurrency exchanges are hardly surprising and not new. One of the most spectacular alleged hacks of a cryptocurrency exchange came to light when Tokyo-based exchange Mt Gox went dark in February 2014, with its founder filing for bankruptcy.
At the time, Mt. Gox's CEO, French national Mark Karpeles, blamed "weaknesses in our system" for allowing hackers to steal 850,000 bitcoins, then worth about $500 million, as well as $28 million in cash from bank accounts.
Japanese authorities launched an investigation into what had been the world's biggest cryptocurrency exchange. Earlier this year Karpeles, now 32, pleaded not guilty to charges that he embezzled funds and illegally manipulated data (see Feds Indict Russian Over BTC-e Bitcoin Exchange).
9. Sustainability Questions Are a Concern
Will the cryptocurrency experiment live on?
Last year, Jamie Dimon, head of JPMorgan Chase, suggested that bitcoins were a "fraud" suitable only for pariah regimes, murderers and thugs. "If you were in Venezuela or Ecuador or North Korea or a bunch of parts like that, or if you were a drug dealer, a murderer, stuff like that, you are better off doing it in bitcoin than U.S. dollars," he said (see Report: North Korea Seeks Bitcoins to Bypass Sanctions).
At the moment, however, investors' thirst for cryptocurrencies appears to know no bounds. The value of bitcoin has continued to exponentially increase, moving beyond $15,000.
One downside of the thirst for cryptocurrencies, however, is that the increased computing power that mining requires results in a very real-world increase in electricity bills.
If mining power consumption keeps increasing at its current pace, some researcherscontend that by July 2019, the bitcoin network will require more energy than currently used by the entire United States, and by February 2020, it will use as much electricity as the entire world does today.
Bitcoin Energy Consumption 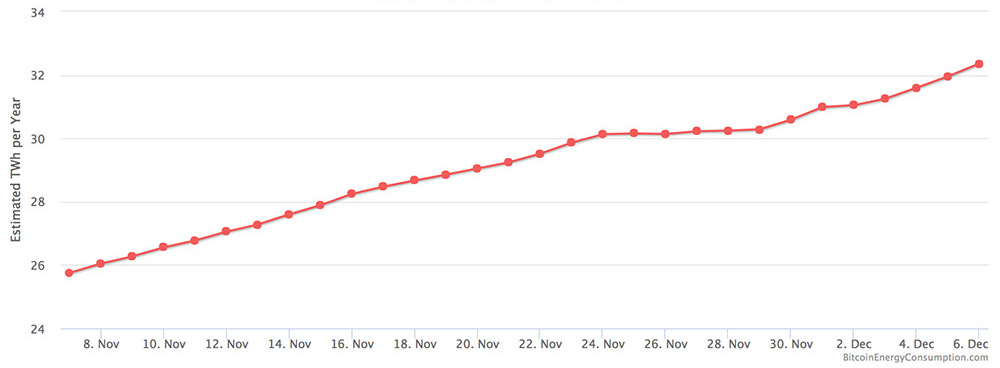

Alan Woodward, a professor of computer science at England's University of Surrey, says such research is proof that the increased appetite for mining is simply not sustainable.
One easy fix, in some respects, would be if the bitcoin bubble were to burst.
As with so many things in life, there are more reasons than one for bitcoin buyers to beware.

No comments:
Post a Comment